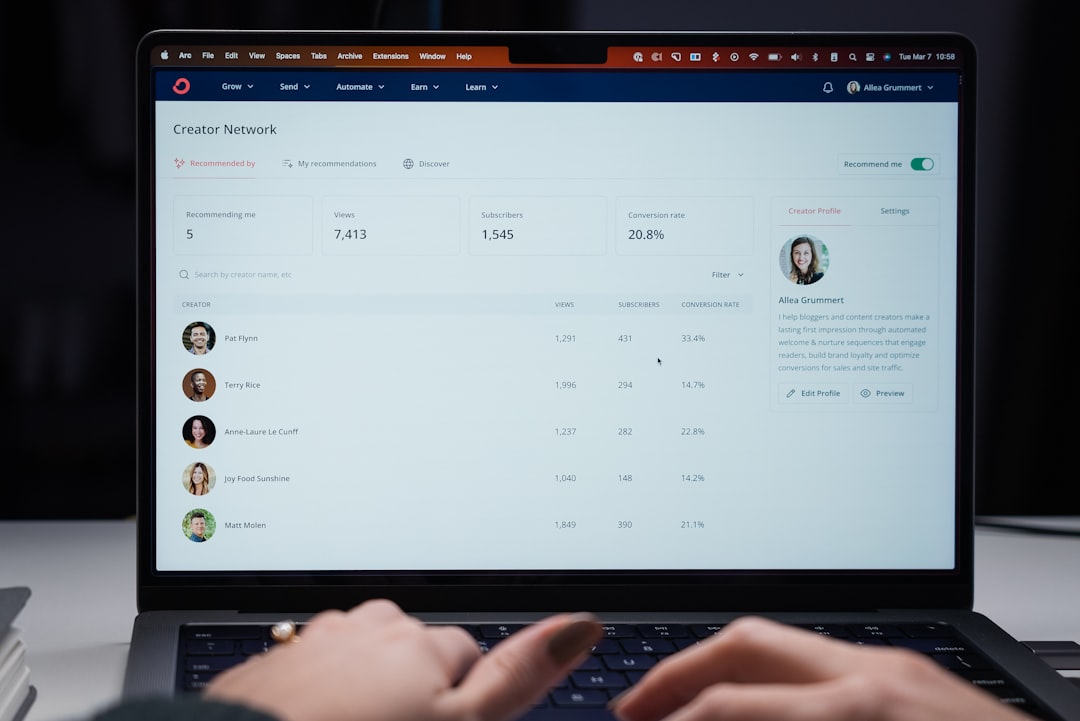
The Social Engineering Toolkit (SET) is a powerful open-source framework designed specifically for penetration testing and security assessments. Developed by TrustedSec, SET is tailored to simulate real-world social engineering attacks, allowing security professionals to evaluate the effectiveness of their organization’s defenses against such threats. By leveraging various attack vectors, SET provides users with the tools necessary to create realistic phishing campaigns, credential harvesting, and other social engineering tactics.
This toolkit is particularly valuable for organizations looking to enhance their security posture by identifying vulnerabilities that could be exploited by malicious actors. SET stands out in the realm of cybersecurity tools due to its user-friendly interface and extensive capabilities. It allows users to craft sophisticated attacks with minimal technical expertise, making it accessible to a broader audience, including those who may not have a deep background in cybersecurity.
The toolkit is continually updated to reflect the latest trends in social engineering and cyber threats, ensuring that users have access to the most effective techniques available. As organizations increasingly recognize the importance of human factors in security, SET has become an essential resource for conducting thorough security assessments.
Key Takeaways
- The Social Engineering Toolkit (SET) is a powerful tool used for simulating social engineering attacks to test the security of an organization’s systems and employees.
- Security testing is crucial for identifying vulnerabilities and weaknesses in an organization’s security infrastructure, and can help prevent real-world attacks and data breaches.
- The Social Engineering Toolkit offers a wide range of features and capabilities, including phishing attacks, credential harvesting, and payload delivery, making it a versatile tool for security testing.
- Using the Social Engineering Toolkit for security testing involves careful planning, ethical considerations, and obtaining proper authorization from the organization being tested.
- Real-world examples have shown the effectiveness of the Social Engineering Toolkit in identifying security vulnerabilities and raising awareness about the importance of security training and awareness within organizations.
Understanding the importance of security testing
Security testing is a critical component of any comprehensive cybersecurity strategy. It involves evaluating an organization’s systems, networks, and applications to identify vulnerabilities that could be exploited by attackers. By conducting regular security testing, organizations can proactively address weaknesses before they are discovered and exploited by malicious actors.
This process not only helps protect sensitive data but also fosters a culture of security awareness among employees, which is vital in today’s threat landscape where human error often plays a significant role in security breaches. Moreover, security testing is essential for compliance with various regulations and standards that govern data protection and privacy. Many industries are subject to strict guidelines that require regular assessments of their security measures.
By utilizing tools like the Social Engineering Toolkit, organizations can demonstrate their commitment to maintaining robust security practices and protecting their customers’ information. In an era where data breaches can lead to severe financial and reputational damage, investing in security testing is not just a best practice; it is a necessity for safeguarding an organization’s future.
Features and capabilities of the Social Engineering Toolkit
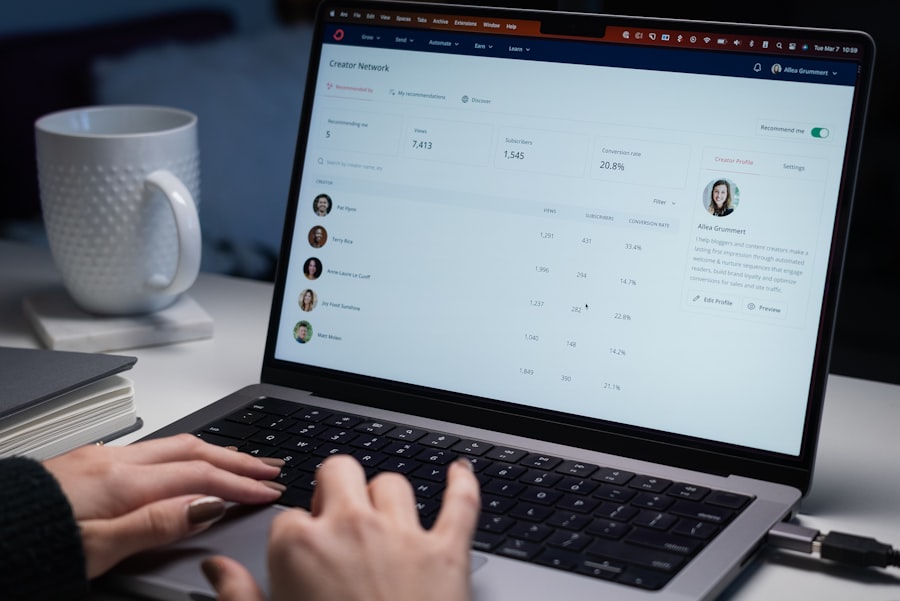
The Social Engineering Toolkit boasts a wide array of features designed to facilitate various types of social engineering attacks. One of its most notable capabilities is its ability to create phishing emails that can be customized to target specific individuals or groups within an organization. This feature allows users to simulate real-world phishing scenarios, providing valuable insights into how employees respond to such threats.
Additionally, SET includes options for creating malicious payloads that can be delivered through various means, such as USB drives or web-based exploits, further enhancing its versatility as a testing tool. Another significant feature of SET is its ability to perform credential harvesting through realistic login pages that mimic legitimate websites. This capability enables security professionals to assess how easily employees might fall victim to phishing attempts and provides an opportunity for targeted training and awareness programs.
Furthermore, SET supports various attack vectors, including social media exploitation and SMS phishing (smishing), allowing users to test their organization’s defenses across multiple platforms. With its comprehensive suite of features, the Social Engineering Toolkit empowers organizations to conduct thorough assessments of their susceptibility to social engineering attacks.
How to use the Social Engineering Toolkit for security testing
| Metrics | Description |
|---|---|
| Number of Phishing Attacks | The total number of phishing attacks conducted using the Social Engineering Toolkit. |
| Success Rate | The percentage of successful social engineering attacks carried out using the toolkit. |
| Types of Attacks | The different types of social engineering attacks performed, such as credential harvesting, website cloning, and payload delivery. |
| Targeted Platforms | The platforms or systems targeted during the security testing, such as email, social media, or web applications. |
| Response Analysis | An analysis of the responses received from the targets, including click rates, data submission, and system compromise. |
Using the Social Engineering Toolkit for security testing involves several steps that require careful planning and execution. First, you need to install SET on your system, which can typically be done on various operating systems, including Linux distributions like Kali Linux. Once installed, you can launch the toolkit and navigate through its user-friendly interface to select the type of attack you wish to simulate.
Whether you choose phishing, credential harvesting, or another method, it’s crucial to define your objectives clearly before proceeding. After selecting your attack vector, you will need to customize your campaign according to your target audience. This may involve crafting convincing email messages or designing realistic login pages that mimic legitimate sites.
It’s essential to ensure that your simulations are as authentic as possible to accurately gauge employee responses. Once your campaign is set up, you can launch it and monitor the results in real-time. Analyzing the data collected during your testing will provide valuable insights into your organization’s vulnerabilities and help you develop targeted training programs to enhance employee awareness and resilience against social engineering attacks.
Real-world examples of successful security testing using the Social Engineering Toolkit
Numerous organizations have successfully utilized the Social Engineering Toolkit to conduct security testing and improve their defenses against social engineering attacks. For instance, a large financial institution employed SET to simulate phishing attacks targeting its employees. By crafting emails that appeared to come from trusted sources within the company, they were able to assess how many employees would click on malicious links or provide sensitive information.
The results revealed a concerning percentage of employees who fell victim to the simulated attack, prompting the organization to implement comprehensive training programs focused on recognizing phishing attempts. Another notable example involves a healthcare organization that used SET to test its staff’s susceptibility to social engineering tactics. By creating fake login pages for commonly used applications within the organization, they were able to measure how many employees would inadvertently enter their credentials into these fraudulent sites.
The findings highlighted significant gaps in employee awareness regarding cybersecurity best practices. As a result, the organization developed targeted training sessions aimed at educating staff about the dangers of social engineering and reinforcing safe online behaviors.
Risks and ethical considerations when using the Social Engineering Toolkit

While the Social Engineering Toolkit is an invaluable resource for security testing, it also comes with inherent risks and ethical considerations that must be addressed. One of the primary concerns is the potential for misuse of the toolkit by individuals with malicious intent. If not properly managed, SET could be employed by cybercriminals to conduct real attacks against unsuspecting victims.
Therefore, it is crucial for organizations to establish clear guidelines and protocols governing the use of SET within their environments, ensuring that only authorized personnel conduct testing in a controlled manner. Additionally, ethical considerations must be taken into account when conducting social engineering tests. It is essential to obtain consent from relevant stakeholders before initiating any testing activities that involve real employees or sensitive data.
Transparency about the purpose of the testing and how the results will be used is vital in maintaining trust within the organization. Furthermore, organizations should ensure that any data collected during testing is handled responsibly and securely, protecting employee privacy while still gaining valuable insights into their security posture.
Alternatives to the Social Engineering Toolkit for security testing
While the Social Engineering Toolkit is a popular choice for simulating social engineering attacks, several alternatives exist that offer similar functionalities for security testing. One such alternative is Gophish, an open-source phishing framework designed specifically for creating and managing phishing campaigns. Gophish provides users with an intuitive interface for designing emails and landing pages while also offering robust tracking features to monitor employee interactions with simulated attacks.
Another noteworthy alternative is Evilginx2, which focuses on advanced phishing techniques such as man-in-the-middle attacks. This tool allows users to capture credentials from users who believe they are logging into legitimate sites while actually being redirected through a malicious proxy server. While Evilginx2 requires more technical expertise than SET or Gophish, it offers unique capabilities for organizations looking to test their defenses against sophisticated phishing tactics.
The future of security testing with the Social Engineering Toolkit
As cyber threats continue to evolve and become more sophisticated, the importance of effective security testing cannot be overstated. The Social Engineering Toolkit remains at the forefront of this effort by providing organizations with a powerful means of assessing their vulnerability to social engineering attacks. Its user-friendly interface and extensive features make it an invaluable resource for both seasoned cybersecurity professionals and those new to the field.
Looking ahead, it is likely that tools like SET will continue to evolve in response to emerging threats and changing attack vectors. As organizations increasingly recognize the critical role that human behavior plays in cybersecurity, investing in tools that facilitate realistic social engineering simulations will become even more essential. By leveraging the capabilities of the Social Engineering Toolkit and similar resources, organizations can foster a culture of security awareness and resilience that will ultimately help protect them against the ever-present threat of cybercrime.
If you’re interested in learning more about the tools and techniques used in cybersecurity, particularly those related to social engineering, you might find the article on the Social Engineering Toolkit (SET) quite enlightening. SET is a popular framework used by cybersecurity professionals to perform penetration tests that simulate real-life security breaches caused by social engineering tactics. For a deeper understanding of how SET is used to test and strengthen security systems against human-centric hacking attempts, you can read more about it in this related article: Exploring the Social Engineering Toolkit. This piece provides insights into the methodology behind SET and its role in critical infrastructure security.
FAQs
What is the Social Engineering Toolkit (SET)?
The Social Engineering Toolkit (SET) is a software framework used for simulating social engineering attacks. It is designed to help security professionals and penetration testers test the security of an organization by emulating the tactics used by malicious hackers.
What are the features of the Social Engineering Toolkit?
The Social Engineering Toolkit includes a wide range of tools and techniques for conducting social engineering attacks, such as phishing, spear phishing, credential harvesting, and more. It also provides options for creating custom attack vectors and generating malicious payloads.
Is the Social Engineering Toolkit legal to use?
The Social Engineering Toolkit is legal to use for legitimate security testing and penetration testing purposes. However, it is important to use the toolkit responsibly and within the boundaries of the law, such as obtaining proper authorization before conducting any testing.
Who can use the Social Engineering Toolkit?
The Social Engineering Toolkit is primarily used by security professionals, penetration testers, and ethical hackers to assess the security posture of an organization. It is not intended for use by individuals without proper training and authorization.
What are the potential risks of using the Social Engineering Toolkit?
Using the Social Engineering Toolkit for unauthorized or malicious purposes can lead to legal consequences, as it involves simulating attacks that could cause harm to individuals or organizations. Additionally, using the toolkit without proper knowledge and training can result in accidental security breaches.